Menguji Keamanan Enkripsi SSL dengan Testssl.sh
Menguji Keamanan Enkripsi SSL dengan Testssl.sh - Kali ini saya akan sharing salahsatu tool yang bisa membantu kalian untuk menguji SSL yang terpasang di server. Testssl.sh adalah tool yang dikembangkan dengan bahasa pemrograman bash dan digunakan untuk menguji SSL. Dengan testssl.sh, kalian bisa mengecek apakah ada kesalahan konfigurasi yang menyebabkan bug, menguji koneksi HTTPS dengan simulasi dari beberapa device berbeda, dan masih banyak fitur lain.
Fitur Utama
- Clear output: you can tell easily whether anything is good or bad
- Ease of installation: It works for Linux, OSX/Darwin, FreeBSD, NetBSD, OpenBSD (needs bash) and MSYS2/Cygwin out of the box: no need to install or to configure something. No gems, CPAN, pip or the like/
- Flexibility: You can test any SSL/TLS enabled and STARTTLS service, not only webservers at port 443
- Toolbox: Several command line options help you to run YOUR test and configure YOUR output
- Reliability: features are tested thoroughly
- Verbosity: If a particular check cannot be performed because of a missing capability on your client side, you'll get a warning
- Privacy: It's only you who sees the result, not a third party
- Freedom: It's 100% open source. You can look at the code, see what's going on and you can change it.
- Heck, even the development is open (github)
Cara Install
Caranya cukup mudah. Tapi sebelum itu pastikan dependensinya sudah terinstall:
- openssl
- git
Oke berikut cara installnya:
git clone --depth 1 https://github.com/drwetter/testssl.sh.git
Cara Pakai
Cara menggunakan testssl.sh cukup mudah. Jalankan
./testssl.sh https://domain.com
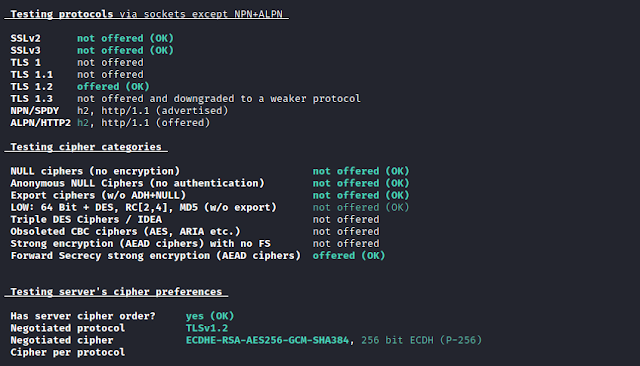
maka hasilnya akan keluar semua. Berikut contoh outputnya:
Namun kalian juga bisa mendapatkan hasil yang lebih rinci dengan menggunakan beberapa perintah yang tersedia. Bisa dicek dengan perintah
./testssl.sh --help
Saat artikel ini ditulis testssl.sh sudah merilis versi 2.9dev. Dan berikut fitur yang diimplementasikan di versi tersebut:
- Using bash sockets where ever possible --> better detection of ciphers, independent on the openssl version used.
- Testing 364 default ciphers (testssl.sh -e/-E) with a mixture of sockets and openssl. Same speed as with openssl only but additional ciphers such as post-quantum ciphers, new CHAHA20/POLY1305, CamelliaGCM etc.
- Further tests via TLS sockets and improvements (handshake parsing, completeness, robustness),
- TLS 1.2 protocol check via socket in production
- Finding more TLS extensions via sockets
- TLS Supported Groups Registry (RFC 7919), key shares extension
- Non-flat JSON support
- File output (CSV, JSON flat, JSON non-flat) supports a minimum severity level (only above supplied level there will be output)
- Support of supplying timeout value for openssl connect -- useful for batch/mass scanning
- Parallel mass testing (!)
- File input for serial or parallel mass testing can be also in nmap grep(p)able (-oG) format
- Native HTML support instead going through 'aha'
- Better formatting of output (indentation)
- Choice showing the RFC naming scheme only
- LUCKY13 and SWEET32 checks
- Check for vulnerability to Bleichenbacher attacks
- Ticketbleed check
- Decoding of unencrypted BIG IP cookies
- LOGJAM: now checking also for known DH parameters
- Check for CAA RR
- Check for OCSP must staple
- Check for Certificate Transparency
- Expect-CT Header Detection
- Check for session resumption (Ticket, ID)
- TLS Robustness check (GREASE)
- Postgres und MySQL STARTTLS support, MongoDB support
- Decodes BIG IP F5 Cookie
- Fully OpenBSD and LibreSSL support
- Missing SAN warning
- Man page
- Better error msg suppression (not fully installed OpenSSL)
- DNS over Proxy and other proxy improvements
- Better JSON output: renamed IDs and findings shorter/better parsable
- JSON output now valid also for non-responsing servers
- Added support for private CAs
- Exit code now 0 for running without error
- ROBOT check
- Better extension support
- Better OpenSSL 1.1.1 support
- Supports latest and greatest version of TLS 1.3, shows drafts supported
Oke mungkin sekian artikel kali ini, semoga bermanfaat.



Posting Komentar untuk "Menguji Keamanan Enkripsi SSL dengan Testssl.sh"
Posting Komentar
Silahkan tinggalkan komentar jika ada masukan, pertanyaan, kritik ataupun dukungan. Namun pastikan untuk berkomentar secara sopan.